开启数据核心转发:
/proc/sys/net/ipv4/ip_forward
Vim/etc/sysctl.conf
net.ipv4.ip_forward=1
iptables 显示扩展multiport,iprange,string,time,connlimit,limit,state
state:与协议无法,匹配建立连接时的状态
连接状态文件:/proc/net/nf_conntrack
/proc/sys/net/nf_conntrack_max #记录上面记录的条数
State连接状态类型:NEW,ESTABLISHED,RELATED,INVALID
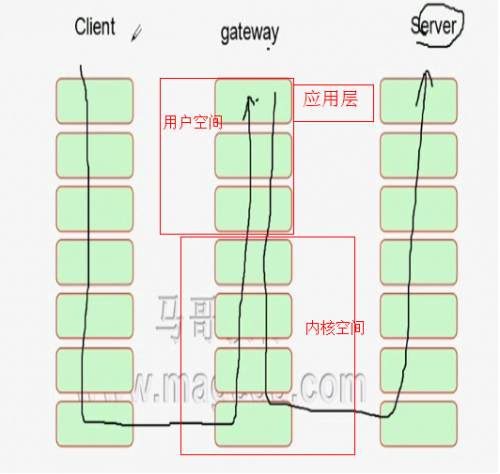
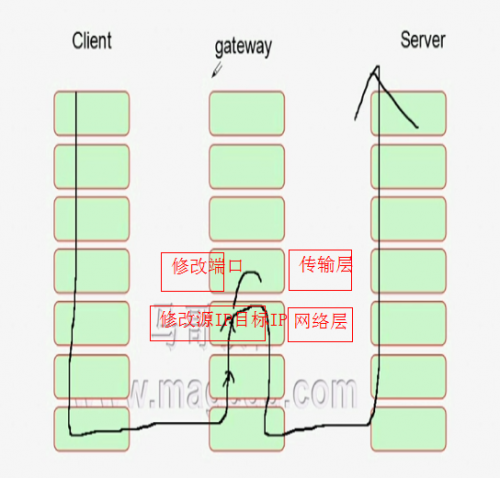
NAT:隐藏内网主机,主要基于安全性,网络层或传输层
Proxy 代理
工作在应用层(7层),代理特定的应用层请求,服务端看到的是代理的IP
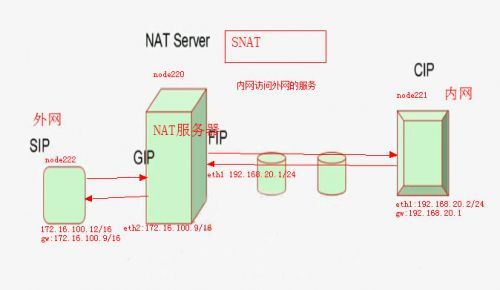
NAT
SNAT:只修改请求报文的源地址 #使内网主机能访问外网 POSTROUTING
源地址转换:
iptables -t nat -A POSTROUTING -s LocalNET !-d Localnet -j SNAT --to-source ExtIP
iptables -t nat -A PORTROUTING -s LocalNET !-d LocalNet -j MASQUERADE
在node221上访问外网node222:
[root@node221 ~]# curl -I http://172.16.100.12:8000
HTTP/1.1 200 OK
Server: nginx/1.4.7
Date: Thu, 14 Sep 2017 08:47:50 GMT
Content-Type: text/html
Content-Length: 27
Last-Modified: Wed, 23 Aug 2017 06:43:16 GMT
Connection: keep-alive
ETag: "599d2404-1b"
Accept-Ranges: bytes
node222外网服务器日志:
172.16.100.9 - - [14/Sep/2017:16:47:40 +0800] "HEAD / HTTP/1.1"200 0 "-" "curl/7.15.5 (i386-redhat-linux-gnu) libcurl/7.15.5OpenSSL/0.9.8b zlib/1.2.3 libidn/0.6.5"
172.16.100.9 - - [14/Sep/2017:16:47:50 +0800] "HEAD / HTTP/1.1"200 0 "-" "curl/7.15.5 (i386-redhat-linux-gnu) libcurl/7.15.5OpenSSL/0.9.8b zlib/1.2.3 libidn/0.6.5"
172.16.100.9 - - [14/Sep/2017:16:51:00 +0800] "HEAD / HTTP/1.1"200 0 "-" "curl/7.15.5 (i386-redhat-linux-gnu) libcurl/7.15.5OpenSSL/0.9.8b zlib/1.2.3 libidn/0.6.5"
node222外网服务器抓包:
[root@node222 logs]# tcpdump -i eth1 host 172.16.100.12
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth1, link-type EN10MB (Ethernet), capture size 96 bytes
16:51:00.135320 IP 172.16.100.9.9394 > 172.16.100.12.irdmi: S108750506:108750506(0) win 5840 <mss 1460,sackOK,timestamp 8299947300,nop,wscale 4>
16:51:40.282076 IP 172.16.100.12.irdmi > 172.16.100.9.9394: S3011140379:3011140379(0) ack 108750507 win 5792 <mss 1460,sackOK,timestamp7837705 829994730,nop,wscale 3>
16:51:40.282326 IP 172.16.100.9.9394 > 172.16.100.12.irdmi: . ack 1 win365 <nop,nop,timestamp 829994732 7837705>
16:51:00.134638 IP 172.16.100.9.9394 > 172.16.100.12.irdmi: P 1:162(161)ack 1 win 365 <nop,nop,timestamp 829994733 7837705>
[root@node220 ~]# iptables -t nat -A POSTROUTING -s 192.168.20.0/24 ! -d192.168.20.0/24 -j SNAT --to-source 172.16.100.9
地址伪装:MASQUERADE
#iptables -tnat -A POSTROUTING -s 192.168.20.0/24 ! -d 192.168.20.0/24 -j MASQUERADE
DNAT:只修改请求报文的目标地址 #端口映射 PREROUTING
目标地址转换:
iptables -t nat -A PREROUTING -dExtIP -p tcp|udp --dport PORT -j DNAT --to-destination Local_server_IP[:PORT]

在node220上做DNAT,将内网node221的22号端口映射到外网接口172.16.100.9上面:
外网主机node222就可以通过sshroot@172.16.100.9 来访问内网node221的SSH服务了
[root@node220 ~]# iptables -t nat -A PREROUTING -d 172.16.100.9 -p tcp--dport 22 -j DNAT --to-destination 192.168.20.2
DNAT端口映射转换:80-->8000
[root@node220 ~]# iptables -t nat -R PREROUTING 1 -d 172.16.100.9 -p tcp--dport 80 -j DNAT --to-destination 192.168.20.2:8000


 CentOS 5.x 6.x iptables NAT 配置
CentOS 5.x 6.x iptables NAT 配置
