显式扩展:必须使用-m选项指定使用的扩展
-m tcp –dport 22 #使用TCP扩展来匹配22号端口
可以使用的显示扩展的类型:
[root@node2~]# rpm -ql iptables | grep "[[:lower:]]\+.so$"
/lib64/xtables/libipt_addrtype.so
/lib64/xtables/libipt_ah.so
/lib64/xtables/libipt_ecn.so
/lib64/xtables/libipt_icmp.so
/lib64/xtables/libipt_realm.so
/lib64/xtables/libipt_set.so
/lib64/xtables/libipt_ttl.so
/lib64/xtables/libipt_unclean.so
查看每一个扩展的帮助文件:
CentOS 6.x
#maniptables
MATCH EXTENSIONS
iptables can use extended packet matching modules. These are loaded in
twoways: implicitly, when -p or --protocol is specified, or with the
-m or --match options, followed by the matching module name; after
CentOS7.x
#maniptables-extensions
MATCHEXTENSIONS
iptables can use extended packetmatching modules with the -m or --match
options, followed by the matching module name; after these, various extra
ommandline options become available, depending on the specific module. You
1. multiport扩展:
以离散方式定义多端口匹配,最多指定15个端口
it can onlybe used in conjunction with -p tcp or -p udp.
源端口:[!] --source-ports,--sportsport[,port|,port:port]...
目标端口:[!] --destination-ports,--dportsport[,port|,port:port]...
目标或源端口:[!] --ports port[,port|,port:port]...
同时开启;22,80端口:
[root@node2~]# iptables -I INPUT -s 192.168.0.0/24 -d 192.168.0.3 -p tcp -mmultiport --dports 22,80 -j ACCEPT
[root@node2~]# iptables -I OUTPUT -d 192.168.0.0/24 -s 192.168.0.3 -p tcp -m multiport--sports 22,80 -j ACCEPT
2. iprange扩展:
指明连续的IP地址范围(不能扩展为整个网络)
iprange
This matches on a given arbitrary rangeof IP addresses.
[!] --src-range from[-to] :指明连续的源IP地址范围
Match source IP in the specifiedrange.
[!] --dst-range from[-to]: 指明连续的目标IP地址范围
Match destination IP in thespecified range.
[root@node2~]# iptables -I INPUT -d 192.168.0.3 -ptcp -m multiport --dports 22:23,80 -m iprange --src-range 192.168.0.2-192.168.0.10 -j ACCEPT
[root@node2~]# iptables -I OUTPUT -p tcp -m multiport --sports 22:23,80 -m iprange--dst-range 192.168.0.2-192.168.0.10 -j ACCEPT
3. string扩展:
检查报文出现的字符串,与给定的字符串匹配
string
This modules matches a given string by using some pattern matching
strategy. It requires a linux kernel>= 2.6.14.
--algo {bm|kmp} #比较算法
Select the pattern matching strategy. (bm = Boyer-Moore, kmp =
Knuth-Pratt-Morris)
--from offset #左侧偏移
Set the offset from which itstarts looking for any matching. If
not passed, default is 0.
--to offset #右侧偏移
Set the offset from which itstarts looking for any matching. If
not passed, default is the packetsize.
[!] --string pattern #从头到尾检查
Matches the given pattern.
[!] --hex-string pattern
Matches the given pattern in hexnotation
配置前可以正常访问:
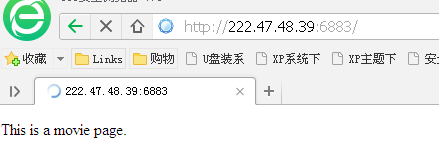 .
.
配置:如果网页内容有’movie’字符串,则拒绝访问
[root@node2html]# iptables -I OUTPUT -m string--algo bm --string 'movie' -j REJECT
[root@node2html]# iptables -L -n -v
Chain OUTPUT(policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
26 8944 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 STRING match"movie" ALGO name bm TO 65535 reject-with icmp-port-unreachable
配置以后网页将无法访问
4. time扩展:
time 基于时间的访问策略:
根据报文到达的时间与指定的时间范围进行匹配
This matches if the packet arrivaltime/date is within a given range.
All options are optional, but are ANDedwhen specified.
--datestartYYYY[-MM[-DD[Thh[:mm[:ss]]]]]
--datestop YYYY[-MM[-DD[Thh[:mm[:ss]]]]]
Only match during the given time, which must be inISO 8601 "T"
notation. The possible time range is 1970-01-01T00:00:00 to
2038-01-19T04:17:07.
If --datestart or --datestop are not specified,it will default
to 1970-01-01 and 2038-01-19,respectively.
--timestart hh:mm[:ss]
--timestop hh:mm[:ss]
Only match during the givendaytime. The possible time range is
00:00:00 to 23:59:59. Leading zeroes are allowed (e.g."06:03")
and correctly interpreted as base-10.
[!] --monthdays day[,day...]
Only match on the given days ofthe month. Possible values are 1
to 31. Note that specifying 31 will of course not match on
months which do not have a 31stday; the same goes for 28- or
29-day February.
[!] --weekdays day[,day...]
Only match on the given weekdays. Possible valuesare Mon, Tue,
Wed, Thu, Fri, Sat, Sun, orvalues from 1 to 7, respectively.
You may also use two-charactervariants (Mo, Tu, etc.).
--utc
Interpret the times given for --datestart, --datestop,--times-
tart and --timestop to be UTC.
--localtz
Interpret the times given for--datestart, --datestop, --times-
tart and --timestop to be localkernel time. (Default)
EXAMPLES. Tomatch on weekends, use:
-m time --weekdays Sa,Su
Or, to match (once) on a nationalholiday block:
-m time --datestart 2007-12-24--datestop 2007-12-27
Since the stop time is actuallyinclusive, you would need the following
stop time to not match the first secondof the new day:
-m time --datestart 2007-01-01T17:00 --datestop
2007-01-01T23:59:59
During lunch hour:
-m time --timestart 12:30--timestop 13:30
The fourth Friday in the month:
-m time --weekdays Fr --monthdays22,23,24,25,26,27,28
(Note that this exploits a certain mathematical property. It is not
possible to say "fourth Thursday ORfourth Friday" in one rule. It is
possible with multiple rules, though.)
例如:
[root@node2~]# iptables -I INPUT -d 192.168.0.3 -p tcp --dport 80 -m time --timestart00:00 --timestop 23:59 -j ACCEPT
[root@node2~]# iptables -L -n -v
Chain INPUT (policy DROP 24 packets, 7464 bytes)
pkts bytes target prot opt in out source destination
17 884 ACCEPT tcp -- * * 0.0.0.0/0 192.168.0.3 tcp dpt:80TIME from 00:00:00 to 23:59:00
5. connlimit扩展(限制每个IP的并发连接数) CentOS7.x
根据每客户端IP (也可以是地址块)做并发连接数数量匹配
Allows you to restrict the number ofparallel connections to a server
per client IP address (or client addressblock).
[!] --connlimit-above n #超过指定的连接数,连接数据大于n
Match if the number of existingconnections is (not) above n.
--connlimit-mask prefix_length # 指明地址网段掩码
Group hosts using the prefixlength. For IPv4, this must be a
number between (including) 0 and 32. For IPv6, between 0 and
128.
Examples:
# allow 2 telnet connections per clienthost
iptables -A INPUT -p tcp --syn --dport 23 -m connlimit
--connlimit-above 2 -j REJECT
# you can also match the other wayaround:
iptables -A INPUT -p tcp --syn --dport 23 -m connlimit !
--connlimit-above 2 -j ACCEPT
# limit the number of parallel HTTPrequests to 16 per class C sized
network (24 bit netmask)
iptables -p tcp --syn --dport80 -m connlimit --connlimit-above
16 --connlimit-mask 24 -j REJECT
# limit the number of parallel HTTPrequests to 16 for the link local
# limit the number of parallel HTTPrequests to 16 for the link local
network
(ipv6) ip6tables -p tcp --syn --dport 80 -s fe80::/64 -m
connlimit --connlimit-above 16--connlimit-mask 64 -j REJECT
限制单IP并发连接限制数量
iptables-I INPUT -p tcp --dport 22 -m connlimit --connlimit-above 3 -j REJECT
6.limit扩展(令牌环过滤器)
基于收发报文的速率做限制
Thismodule matches at a limited rate using a token bucket filter. A
rule using this extension will match until this limit is reached
(unless the ‘!’ flag is used). It can be used in combination with the
LOGtarget to give limited logging, for example.
--limit rate[/second|/minute|/hour|/day] #限制速率
Maximum average matching rate: specified as a number, with an
optional ‘/second’, ‘/minute’, ‘/hour’, or ‘/day’ suffix; the
default is 3/hour.
--limit-burst number #将开始没有做限制时的最大可接受的值
Maximum initial number of packets to match: this numbergets
recharged by one every time the limit specified above is not
reached, up to this number; the default is 5.
[root@node2~]# iptables -A INPUT -d 192.168.0.3 -p icmp --icmp-type 8 -m limit--limit-burst 5 --limit 30/minute -j ACCEPT
[root@node2~]# iptables -A OUTPUT -s 192.168.0.3 -p icmp --icmp-type 0 -j ACCEPT
7.state扩展(连接追踪机制非常消耗资源)TCP的会话超时时间是2小时
根据连接追踪机制检查连接间的状态,来控制连接的匹配检查
不同协议或连接类型追踪的时长
/proc/sys/net/netfilter/
在内存中记录连接状态:在内核中记录连接
源IP 目的IP 源端口 目标端口 协议 计数器
调整连接追踪功能所能够容纳的最大的连接数量
/proc/sys/net/nf_conntrack_max
[root@node2~]# cat /proc/sys/net/nf_conntrack_max
31748
查看当前已追踪了那些连接:
[root@node2~]# cat /proc/net/nf_conntrack
ipv4 2 tcp 6 431999 ESTABLISHED src=192.168.0.3 dst=58.23.25.144 sport=22dport=2077 src=58.23.25.144 dst=192.168.0.3 sport=2077 dport=22 [ASSURED]mark=0 secmark=0 use=2
INVALID
meaning that the packet isassociated with no known connection
NEW meaning that the packet has started a new connection, or otherwise associ-
ated with a connection which hasnot seen packets in both directions, and
ESTABLISHED
meaning that the packet is associated with a connection which has seen
packets in both directions,
RELATED
meaning that the packet isstarting a new connection, but is associated
with an existing connection, such as an FTP data transfer, or anICMP
error.
SNAT A virtual state, matching if the original source address differs from the
reply destination.
DNAT A virtual state, matching if the original destination differs from the
reply source.
Statuses for --ctstatus:
NONE None of the below.
state
This module, when combined with connection tracking, allows access to theconnec-
tion tracking state for this packet.
[!] --state state
Where state is a comma separatedlist of the connection states to match.
Possible states are INVALIDmeaning that the packet could not be identified
for some reason which includesrunning out of memory and ICMP errors which
don’t correspond to any known connection, ESTABLISHED meaning that the
packet is associated with aconnection which has seen packets in both
directions, NEW meaning that the packet hasstarted a new connection, or
otherwise associated with aconnection which has not seen packets in both
directions, and RELATED meaning that the packet is starting a new connec-
tion, but is associated with anexisting connection, such as an FTP data
transfer, or an ICMP error.
可追踪的连接状态:
NEW:新发出的请求,连接追踪模板中不存在些连接相关的信息条目,因此,将其识别为第一次发出的请求
ESTABLISHED:NEW状态之后,连接追踪模板中为其建立的条目失效之前期间内所进行的通信的状态
RELATED:相关的连接FTP(数据连接由命令连接建立之后才能使用数据连接)
INVALIED:无法识别的连接
反弹式木马:通过扫描本的开放的端口,通过开放的端口来与远程主机建立连接
80端口只会响应请求,不会主动发起请求,通过禁用80端口的NEW功能来防止反弹式木马
本地的SSH,apache服务器80端口,只能响应远程的请求,不可能主动向远程发起连接
INPUT 放行:NEW ESTABLISHED
[root@node2~]# iptables -I INPUT -d 192.168.0.3 -p tcp --dport 22 -m state --stateNEW,ESTABLISHED -j ACCEPT
OUTPUT 放行:ESTABLISHD
[root@node2~]# iptables -I OUTPUT -s 192.168.0.3 -p tcp --sport 22 -m state --stateESTABLISHED -j ACCEPT
[root@node2~]# iptables -L -n
Chain INPUT(policy DROP)
target prot opt source destination
ACCEPT tcp -- 0.0.0.0/0 192.168.0.3 tcp dpt:22 state NEW,ESTABLISHED
ACCEPT tcp -- 192.168.0.3 0.0.0.0/0 tcp spt:22 state ESTABLISHED
开启ICMP的连接状态追踪:
[root@node2~]# iptables -A INPUT -d 192.168.0.3 -p icmp --icmp-type 8 -m state --stateNEW,ESTABLISHED -j ACCEPT
[root@node2~]# iptables -A OUTPUT -s 192.168.0.3 -p icmp --icmp-type 0 -m state --stateESTABLISHED -j ACCEPT
优化:
在入接口上,只要是ESTABLISHED的,都放行:
[root@node2 ~]# iptables -I INPUT -mstate --state ESTABLISHED -j ACCEPT
在出接口上,对只要能通过INPUT进来的报文,都可以通过OUTPUT出去
[root@node2 ~]# iptables -I OUTPUT -mstate --state ESTABLISHED -j ACCEPT
只检查报文的新建立的连接请求:
[root@node2~]# iptables -I INPUT 2 -d 192.168.0.3 -p tcp -m multiport --dports 22,80 -mstate --state NEW -j ACCEPT


 iptables扩展及使用
iptables扩展及使用
