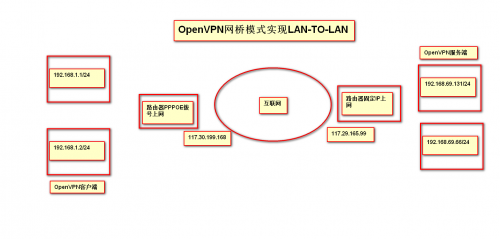
使用openvpn的桥接模式,就可以让vpn客户端和VPN服务端的IP在同一网段。
客户端连接VPN后,分配IP地址:192.168.69.201
服务器所在的网络为:192.168.69.0/24
服务器IP地址:192.168.69.131
功能:客户端连接VPN后,可以ping通VPN服务器所在的私有网段的所有主机
以下的配置是在安装完成openvpn之后
服务启动方式:
先运行脚本:/usr/local/openvpn/config/bridge-start
再启动服务:serviceopenvpn start
2.bridge-start配置
#!/bin/sh
#################################
# Set up Ethernet bridge on Linux
# Requires: bridge-utils
#################################
# Define Bridge Interface
br="br0"
# Define list of TAP interfaces to be bridged,
# for example tap="tap0 tap1 tap2".
#这边的tap0要和server.conf中的dev tap0对应
tap="tap0"
# Define physical ethernet interface to be bridged
# with TAP interface(s) above.
eth="eth0"
eth_ip="192.168.69.131"
eth_netmask="255.255.128.0"
eth_broadcast="192.168.127.255"
for t in $tap; do
openvpn --mktun --dev $t
done
brctl addbr $br
brctl addif $br $eth
for t in $tap; do
brctl addif $br $t
done
for t in $tap; do
ifconfig $t 0.0.0.0 promisc up
done
ifconfig $eth 0.0.0.0 promisc up
ifconfig $br $eth_ip netmask $eth_netmask broadcast $eth_broadcast
#在运行文件后,桥接IP和eth0物理同时会有IP地址,这时将物理IP地址清空,并加上默认网关
sleep 3
ifconfig eth0 0
sleep 3
route add default gw 192.168.66.1
3.bridge-stop配置
#!/bin/sh
####################################
# Tear Down Ethernet bridge on Linux
####################################
# Define Bridge Interface
br="br0"
# Define list of TAP interfaces to be bridged together
tap="tap0"
ifconfig $br down
brctl delbr $br
for t in $tap; do
openvpn --rmtun --dev $t
done
#在运行此文件后,服务器无法获取由DHCP指派的网络,加以下命令
service network restart
4.server.conf配置文件
port 1194
proto tcp
dev tap0
ca /usr/local/openvpn/config/ca.crt
cert /usr/local/openvpn/config/server.crt
key /usr/local/openvpn/config/server.key # This file should be kept secret
dh dh2048.pem
ifconfig-pool-persist ipp.txt
server-bridge 192.168.69.131 255.255.255.0 192.168.69.200 192.168.69.250
push "route 192.168.66.0 255.255.255.0"
keepalive 10 120
cipher AES-256-CBC
comp-lzo
user nobody
group nobody
persist-key
persist-tun
status /var/log/openvpn/openvpn-status.log
log /var/log/openvpn/openvpn.log
verb 3
#以下配置文件开启用户名和密码认证
auth-user-pass-verify /usr/local/openvpn/config/checkpsw.shvia-env
client-cert-not-required
username-as-common-name
script-security 3
网络信息:
[root@node66131 config]# ifconfig
br0 Link encap:Ethernet HWaddr 2C:FD:A1:5D:84:07
inetaddr:192.168.69.131 Bcast:192.168.127.255 Mask:255.255.128.0
inet6addr: fe80::2efd:a1ff:fe5d:8407/64 Scope:Link
UPBROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RXpackets:1977069 errors:0 dropped:0 overruns:0 frame:0
TXpackets:37752 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RXbytes:133220859 (127.0 MiB) TXbytes:27364255 (26.0 MiB)
eth0 Link encap:Ethernet HWaddr 2C:FD:A1:5D:84:07
inet6addr: fe80::2efd:a1ff:fe5d:8407/64 Scope:Link
UPBROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1
RXpackets:2167457 errors:0 dropped:0 overruns:0 frame:0
TXpackets:56324 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RXbytes:206660856 (197.0 MiB) TXbytes:30124583 (28.7 MiB)
lo Linkencap:Local Loopback
inetaddr:127.0.0.1 Mask:255.0.0.0
inet6addr: ::1/128 Scope:Host
UPLOOPBACK RUNNING MTU:65536 Metric:1
RXpackets:374 errors:0 dropped:0 overruns:0 frame:0
TXpackets:374 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RXbytes:46292 (45.2 KiB) TX bytes:46292(45.2 KiB)
tap0 Linkencap:Ethernet HWaddrA2:0C:78:42:B8:36
inet6addr: fe80::a00c:78ff:fe42:b836/64 Scope:Link
UPBROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1
RX packets:1407 errors:0 dropped:0overruns:0 frame:0
TXpackets:1935925 errors:0 dropped:10040 overruns:0 carrier:0
collisions:0 txqueuelen:100
RXbytes:158956 (155.2 KiB) TXbytes:149774507 (142.8 MiB)
[root@node66131 config]# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
192.168.0.0 0.0.0.0 255.255.128.0 U 0 0 0 br0
0.0.0.0 192.168.66.1 0.0.0.0 UG 0 0 0 br0
[root@node66131 config]# brctl show
bridge namebridgeid STP enabledinterfaces
br0 8000.2cfda15d8407 no eth0
tap0
[root@node66131 config]# ss
State Recv-Q Send-Q LocalAddress:Port PeerAddress:Port
ESTAB 0 0 192.168.69.131:ssh 192.168.66.68:50554
ESTAB 0 0 192.168.69.131:ssh 192.168.66.68:50511
ESTAB 0 2007 192.168.69.131:openvpn 117.30.199.168:19769
ESTAB 0 52 192.168.69.131:ssh 192.168.66.68:50412
ESTAB 0 0 192.168.69.131:ssh 192.168.66.68:50498
配置openvpn使用账号、密码方式验证登录:
第一步:修改Server端配置文件:
在最后面添加以下文件:
vim /usr/local/openvpn/config/server.conf
在文件最后面添加以下配置:
auth-user-pass-verify /usr/local/openvpn/etc/checkpsw.sh via-env
client-cert-not-required
username-as-common-name
script-security 3
注:如果加上client-cert-not-required则代表只使用用户名密码方式验证登录,如果不加,则代表需要证书和用户名密码双重验证登录!
checkpsw.sh下载地址:http://openvpn.se/files/other/checkpsw.sh
将文件放到以下目录下:
[root@node66131 config]# pwd
/usr/local/openvpn/config
[root@node66131 config]# ls
bridge-start ca.crt checkpsw.sh ipp.txt server.conf server.crt ta.key
bridge-stop ca.key dh2048.pem psw-file server.conf.bak server.key
[root@node66131 config]# chmod 755 checkpsw.sh #添加执行权限
第二步:修改checkpsw.sh里的相应参数,主要改下PASSFILE和LOG_FILE两个变量就可以了
[root@node66131 config]# cat checkpsw.sh
#!/bin/sh
###########################################################
# checkpsw.sh (C) 2004 Mathias Sundman<mathias@openvpn.se>
#
# This script will authenticate OpenVPN usersagainst
# a plain text file. The passfile should simplycontain
# one row per user with the username first followedby
# one or more space(s) or tab(s) and then thepassword.
PASSFILE="/usr/local/openvpn/config/psw-file"
LOG_FILE="/var/log/openvpn/openvpn-password.log"
TIME_STAMP=`date "+%Y-%m-%d %T"`
###########################################################
if [ ! -r "${PASSFILE}" ]; then
echo"${TIME_STAMP}: Could not open password file \"${PASSFILE}\" forreading." >> ${LOG_FILE}
exit 1
fi
CORRECT_PASSWORD=`awk'!/^;/&&!/^#/&&$1=="'${username}'"{print $2;exit}'${PASSFILE}`
if [ "${CORRECT_PASSWORD}" = ""]; then
echo"${TIME_STAMP}: User does not exist: username=\"${username}\",password=\"${password}\"." >> ${LOG_FILE}
exit 1
fi
if [ "${password}" ="${CORRECT_PASSWORD}" ]; then
echo"${TIME_STAMP}: Successful authentication:username=\"${username}\"." >> ${LOG_FILE}
exit 0
fi
echo "${TIME_STAMP}: Incorrect password:username=\"${username}\", password=\"${password}\".">> ${LOG_FILE}
exit 1
第三步:新建用户和密码认证文件,psw-file(这里的文件就是server.conf那个文件,注意存放时,路径和配置文件时的一致)
创建文件:
#touch /usr/local/openvpn/config/psw-file
vim psw-file
test 123456 (前面是用户后面是密码)
注:这里 psw-file的权限,尽量小点
chmod 400 psw-file
chown nobody.nobody psw-file
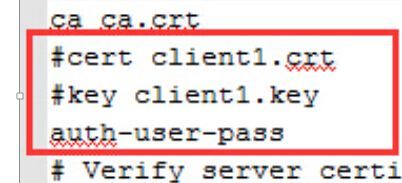
第四步:修改客户端配置文件:client.conf(或者client.ovpn)
vim client.ovpn
注销掉这两行
#cert client1.crt
#key client1.key
再添加这一行,添加这行,就会提示输入用户名和密码
auth-user-pass
auth-nocache
如图:(更改过后的)
接下来,就可以测试了^_^


 OpenVPN网桥模式实现LAN-TO-LAN+帐号密码认证
OpenVPN网桥模式实现LAN-TO-LAN+帐号密码认证
